
If you’re reading this post, you've probably been using the Internet for a couple of years, or perhaps your whole life - Email, funny cat videos, school stuff, work stuff, wedding invitations, the usual stuff. Maybe you don’t think you’ve made enough of a splash to get targeted by hackers, hate mobs, or worse. But, hypothetically, let’s say you find yourself in the crosshairs.
After all, it doesn't take much to be targeted. Maybe you spoke up about a controversial topic, or you were related to someone who did. Maybe it wasn't really anything you said, but you turned out to be an easy 'mark' because you're still using the same passwords from high school, or someone was able to answer your security questions by snooping your social media. Once your identity has been compromised online and you find yourself unable to login to your Facebook or email account, that sinking feeling in your stomach sets the tone of what’s to come; you're in trouble.
Hopefully, you won’t find yourself in this situation. But as life online dialogue becomes increasingly focused on hot button issues like religion, social issues, and Top 40 music, it pays off to make sure that what’s yours will remain yours. Keeping information out of the wrong hands used to be difficult, but with new tools and platforms like cloud computing and storage, it's becoming easier to quickly boost tech literacy levels of everyday people. The right tools, tips, and habits can help you stay safe, keep track of what's going on, and help you come out clean on the other side. After reading this guide, it’s our hope that you will have the knowledge you need to stay secure online in the event of being targeted by harassers, hackers, or anyone who may be trying to compromise your online security.
If you feel anything to be missing or have specific questions, feel free to email us at help@crashoverridenetwork.com.
Most of us aren't taught how to create secure passwords. It’s tempting to use the same easy-to-remember password for multiple websites, but that can create a domino effect and end up compromising your entire online identity if discovered. Insecure passwords like "123456", "password" and "iloveyou" are easy to remember, but set you up for trouble. If you’re like most people, you don't think anyone would be interested in anything on your computer or smartphone, but being interesting isn’t the only thing that can make you a target. Sometimes, it may be the very act of being lax with security practices, or being made an easy mark by a website’s security flaws; other times, you might just be targeted for kicks or practice by trolls and hackers. The reasons can be diverse, but the result can be singularly devastating.
Before we dive into managing your passwords, there are a few bits of common wisdom to ingest:
- Your password should be over six characters long (and here’s why). A six letter password can be cracked in less than 15 minutes, depending on the targeted system.
- Think “passphrase,” not “password.” (We’ll revisit this in a moment.)
- Stop trying to remember all your passwords! Some people try to use memory tricks like cyphers and site name integration, but this can still be insecure if someone figures out your patterns.
- Never, ever store all of our passwords in a plaintext file, in any location, anywhere, ever. C’mon. It’s 2015. Let that practice go the way of NetZero and Geocities.
In this section, we are going to introduce you to password managers: Apps that hold all your passwords securely in one place with a master passphrase.
Password Managers: One Keyring To Rule Them All
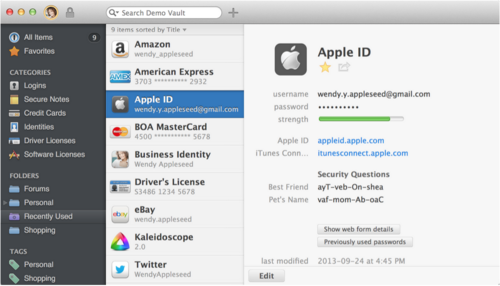
A password manager is a piece of software that holds all your passwords and requires one unique master password in order to gain access. Think of like Online Security Inception: Passwords within a password. You have to break in to break in.
Needless to say, this creates the issue of having a treasure trove of security information stored in one central location, which makes it a valuable prize for anyone trying to compromise your online security. To protect it, you’re going to want a reliable manager and a big, mean mother of a master password to hold it all together, something uncrackable by brute force and tough to guess by either computer or human. This would be a good time to learn how to make Awesome Passwords from Scratch™.
In this comic strip by xkcd, Randall Munroe illustrates the problem of how most people try to create secure passwords:
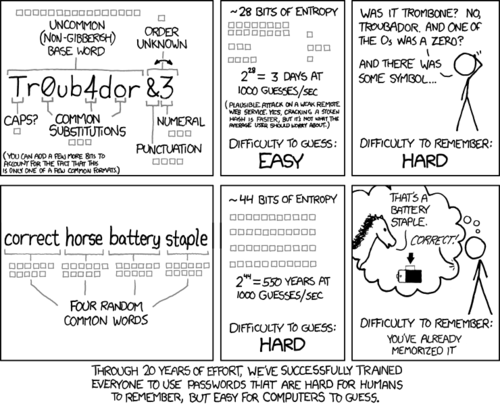
As illustrated above, what many tech-savvy people do is use a cypher, replacing letters with numbers and special characters, sometimes integrating the name of the service the password is intended for. While this creates technically robust and unique passwords, it still has its faults. Using the same cypher across multiple sites still makes it easy for people to guess your passwords if they can glean the patterns you’re using, and an inconsistent cypher is still a pain to recall. This is why many people have negative feelings towards unique passwords in general.
Passphrases are easier to remember, and also happen to be more secure, especially when the words are unrelated (as opposed to, say, song lyrics or famous quotes). It’s a good habit to get into, and definitely recommended as a method of generating a password to secure your manager of choice.
Speaking of which....
Password Manager Options
Password managers have a lot of benefits. At their most basic level, they centralize all your passwords in one area so you can always find them. Many offer password access via the web and on your mobile device. Why type your password each time when you can have it automatically typed for you?
Several of these apps feature an auto-login feature so that when you visit a site, it's not necessary to retype your password each time.Some even include the option of performing a security audit on your existing passwords, testing not only their complexity, but also if the websites in your manager have recently experienced a security breach (like Sony, Target and LinkedIn have from time to time.)
With your shiny new password manager, you can generate long, technically complex random passwords (typically up to 100 dual-case alphanumeric with special characters). Since the passwords for each site are unique, one site being compromised doesn’t mean losing access to the rest. There are many password managers available, but there are a few of note that we highly recommend.
1password (Mac, Windows, iOS, Android): With an excellent UI, mobile access, device syncing, and browser plugins that make storing and generating new passwords a breeze, 1password is a great choice. It stores information locally (that is, on the computer you install it on), so remember to make sure you are backing it up - there’s also an option to sync your 1password to Dropbox if you’re comfortable doing so. Make sure you have 2-factor authentication turned on on Dropbox if you use this option! 1Password is $50 for a desktop license, but the mobile version is free.
LastPass (Web, browser extension, iOS, Android, Blackberry, Windows Phone): If you’re looking for the swiss army knife of password managers, look no further. LastPass is an incredible and convenient password manager. It’s web-based (but does offer offline access), so all your passwords are securely synced to the cloud. Like 1Password, LastPass also offers browser plugins (for Internet Explorer, Firefox, Chrome, Safari, and Opera), and offers mobile versions of the password manager. LastPass also has all sorts of “enterprise” features that let you manage passwords across an organization or company. Where LastPass stands out is raw power and plethora of security options. For those of you who like to get into the geeky details, LastPass offers services like multifactor authentication, password porting, and device whitelisting. You’re also not done once LastPass stores your password - you can be notified when high profile websites are compromised, plus have your existing passwords analyzed to see if their hash was included in the breach. The basic version is free, and Premium (which includes the smartphone client) is $12/year (and recommended).
Keepass (Windows, Linux, browser extension, iOS, Windows phone, Blackberry, PalmOS): As one of the first password managers to hit the market (and also open source), Keepass is a bit less stylish and not as feature-rich as other options, but it makes up for that with the wide variety of platforms it can be run on. It is nonetheless a very powerful and practical password management software. With the project being completely free and open source, it allows people to build Keepass for many different environments. Storage is local, so we recommend you keep your password manager and its associated vaults backed up.
Piece of Paper (Physical): While less convenient than other methods, writing passwords down on physical paper is a tried and true method of password wrangling. While it may seem like a simple, free, no-hassle solution, there are some very important caveats to consider. You’ve likely read advice telling you to “never write down your passwords.” This is because we, as human beings, have a bad habit of leaving the password to a secure computer sitting on the desk next to the computer that is being secured. Physical copies of passwords can be kept secure just like any small, valuable item you own. Treat passwords in paper form the same as money, passports, legal documents, your great grandmother’s antique pearl earrings, the deed to old man Withers’ silver mine, and of course, the keys to your house. Don’t leave passwords on the desk at work or taped to your monitor. This is what characters do in video games just before your crack their work computers wide open.

Don’t be that guy.
For those of you wanting an extra layer of security on top of this, consider using different usernames and emails to log into services. If there’s an account you absolutely cannot deal with having compromised, consider using an email that is only used as a login to that specific account, that you do not make mention of anywhere else.
Finally, keep it regular - Just like changing the filter in your furnace or the wiper blades on your car, consider setting up a recurring calendar event to review your security situation by regularly doing things like checking the audit logs on your website (guide on how to do this for Google located here, for instance). Some people get into the habit of also changing their passwords regularly, but if you do, make sure you’re not re-using old passwords (which shouldn’t be a problem with those generated by a password manager). If you feel your situation warrants a higher level of vigilance, please don’t hesitate to do your due diligence more frequently, especially if you’ve experienced a compromised account. Password managers like Keepass can set expiry dates on entries to remind you to do this.
Multifactor Authentication
Armed with a good password manager, you’ve already taken the first step in securing your online information, so let's take a look at another thing to be aware of - websites can be hacked and their password databases compromised, which can also put your information at risk if you don’t catch it in time. This is where multifactor authentication comes in.
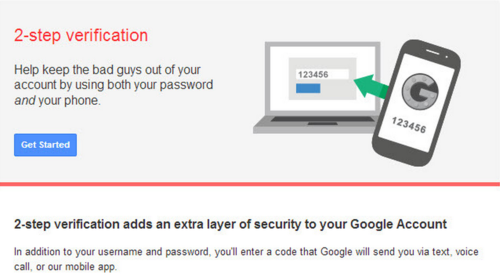
Multifactor authentication (or MFA/2-Factor Authentication/2-Step Verification) is a method of requiring the person who wants access an account to verify their identity in more than one way. While this technology has been around for more than 20 years and is deployed in many large organizations, it is increasingly becoming available to individuals to protect their various accounts from social platforms like Twitter, Facebook and LinkedIn to online banking and gaming-related services. Google, for example, allows you to enable multifactor authentication for their Gmail and Google Apps products.
Multifactor authentication requires a short-lived one-time code in addition to your password. You can get these codes in a number of ways:
- - Sent to your mobile device as a text message.
- - Generated as a text list of one-time “backup codes” to carry with you in case you were to lose your phone or authentication device. Services such as Google offer this service.
- - Generated with authentication apps such as Google Authenticator or Authy. Instead of a code, you are given a login prompt on a mobile app in order to gain access to an account.
One important caveat: don’t use Google Voice to receive reset texts; if your Google Account is compromised, that grants the attacker access to those texts. This has been used in a number of targeted attacks, and severely undermines the effectiveness of two-factor auth.
Typically this process is experienced as logging in with your password, and then being prompted for the code or login verification. What this means is that a hacker would need access to both your password and your multifactor device (such as your mobile phone) in order to compromise your account. This one of the strongest available deterrents against hacking attempts, and is relatively simple to set up for most services that offer it. The EFF has a guide here on how to do so for some of the most popular services on the web.
There is a constantly updated list of sites that offer two-factor authentication at https://twofactorauth.org/; We highly recommend going down the list and enabling 2-factor for any sites you may use that support it, and when considering new services to use, you can consult the site to see which ones already support it. If you use a service shared across multiple users (such as a shared Dropbox, Basecamp project, or files shared across Google Apps), remember that everyone should be enabling multifactor authentication. Your security is only as strong as its weakest link - that includes accounts that may be shared across your friends and family, so encourage the people you know to utilize this form of security as well!
Multifactor Hard Mode: Yubikeys

Want to get even more secure? Pick up a Yubikey! These small USB dongles allow you to "unlock" and access your online account with several providers including Google, Dreamhost, LastPass, and a large number of other services listed on the Yubico website. For the more geek-minded, the NEO model (pictured) supports near-field capabilities (for mobile devices) as well as FIDO U2F and OTP (One Time Password) protocols. Think of it like a personal smart-card; It’s recognized on your computer as a USB keyboard, and when the button is pressed, it will generate an OTP that a service responds to, and can sometimes even be configured to only allow access to an account when the Yubikey is physically plugged into the USB port. Some platforms and operating systems don’t support the Yubikey automatically, but Yubico offers custom programs, drivers, and an active help forum to bridge the gap.
Once a Yubikey is enabled with your service, the reward is an impressively secure setup. Like we described above with two-factor authentication, when you connect your Yubikey to a service, the only way to get back in is with your username, password, and the Yubikey physically inserted into your computer's USB port. Sounds pretty good, huh? For rockstar level password security, use your Yubikey with LastPass (the password manager we mentioned in the last section). You can also configure your Yubikey for all sorts of different password protocols, or even to generate a single, static character string you can use as a master password for any other password manager. Plus, you can wear them on a chain like a necklace! Fancy.
Of course, all multifactor security runs the risk of being inaccessible if you lose your authentication device. For this reason, we suggest you have multiple devices that you can authenticate with. For instance, when buying Yubikeys, consider buying two, configuring both of them identically, and then keeping one stored somewhere safe in case you lose the first.
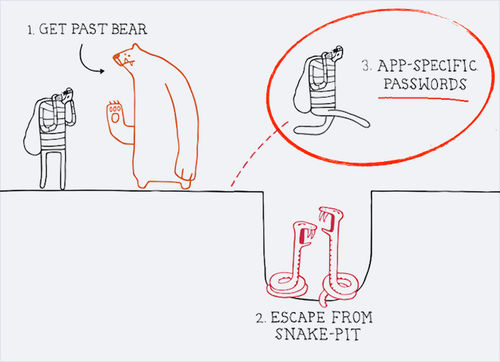
App Passwords and Third Party Access
One potentially tricky issue posed by two-factor authentication is when you want to use an app that don’t have a place to accept multifactor codes at login. Some applications store OAuth tokens when it’s used to log in for the first time, meaning it’s “authenticated” for future logins without storing the password. Other apps, however, don’t do this, and instead store a password for use every time you log in. This becomes a problem when logins require ever-changing multifactor authentication codes. What are you supposed to do?
In these cases, you might be tempted to generate app-specific passwords. These are unique static password that grant full access to the account (here is a guide on using them for Google accounts, for instance), used to help apps that use password storage circumvent the need for a multifactor code. The assumption is that the login is kosher since you need to be logged into the service to generate the app passwords in the first place. They’re also generally only around 16 characters long, which is a major time saver when you consider the alternative of trying to enter a 100-character alphanumeric password to give your Playstation Vita access to your Facebook.
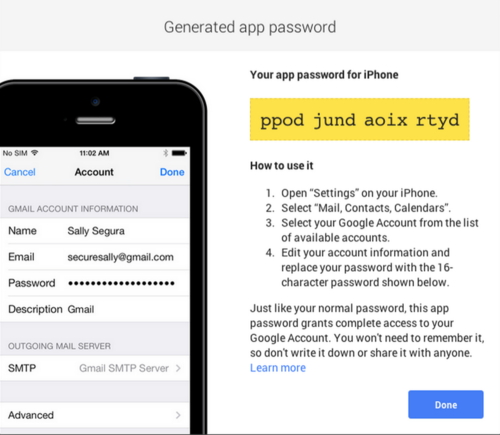
While these are useful and convenient, there are some major security concerns to keep in mind with app passwords. There’s further reading on the how and why here, but the short story is that these passwords aren’t necessarily application-specific, they’re just new master passwords to your account - passwords that automatically bypass multifactor authentication, we might add - and they’re by no means tied to a specific application (in that many applications can use the same app password).
You may be wondering what the point is to having these, then. They allow you to use multifactored services with apps that don’t support OAuth (a trend that many developers are thankfully moving away from), and that’s better than no multifactor auth at all, but they are still a major security flaw. If someone breaks into your account, they may generate app passwords for backup measures of intrusion, or a database leak may reveal an app password that allows a hacker to bypass your multifactor security.
via duo security
The best way to avoid this? Don’t use application specific passwords. Seriously, they’re awful, and really just a stopgap until developers catch up.
But, if you absolutely must use them for whatever services you need, you should be regularly checking them and revoking unfamiliar passwords or those used by services with less-than-stellar security, with an ultimate goal of getting down to few-to-none. Limit your use of them as best you can, and from time to time, see if the services you are using have integrated OAuth support, as most major services have.
While not as insecure as application-specific passwords, it would also make sense to occasionally review third-party apps that may have permission to access or modify your main accounts such as Facebook, Twitter, and Google. There’s a guide here for doing this on most major services. While it may not allow full access to your accounts in the way application-specific passwords do, one of these third-party apps getting compromised could give hackers posting rights to your social media or even access to your data, depending on what the app pulls from your account to function.
Physical Access: Wiping Data Securely and Remotely
Being able revoke permissions and passwords is especially useful if a device that uses them becomes lost or stolen. Speaking of which...
While we’ve focused on protecting your passwords and data from remote intrusion, there’s one point of ingress that’s far more difficult to avoid by these security measures: Hackers gaining physical access to the data. This can include someone finding your lost phone, acquiring a discarded hard drive that wasn’t securely wiped, or straight-up physical theft of a device. This is also why many reputable data centers have physical security for their servers.

Not pictured: reputable data center
If you lose physical possession of your phone or computer with all of your accounts logged in, your data is in danger. Don’t be lulled into thinking your password or your secret swipe pattern will keep the thieves at bay - PIN codes are easy to compromise via brute force (only 10,000 possible combinations), and pattern-based lock mechanisms can be gleaned by simply reading smudges on the screen. This is doubly troubling if it’s a mobile device to which two-factor authentication codes are sent, as it allows whoever is in possession of the device to log into your other accounts if they can retrieve or reset the password.
To combat this, mobile OSes like iOS and Android offer the ability to wipe your phone remotely should it become lost or stolen (guides here and here, respectively). Windows Phone and Blackberry offer this functionality as well (guide here). There are also a number of third-party applications such as Lookout Security and Prey which can track, wipe, and encrypt your devices from a web interface, but they must be installed in advance of you losing your device - take some time to do this now if you’re concerned.
This is also a good reason to wipe your hard drives or phones completely if you intend to discard them, as it’s not unheard of for people to try and compromise your data by dumpster-diving for discarded electronics or restoring old mobile phones and hard drives you may have written off. Lifehacker has a guide here to securely erasing all data on your mobile phone here, and one for your computers here.
Social Engineering
Of course, for all the techno-wizardry we throw at account security, the simplest solutions are often the most effective. All too often, people looking to break into your accounts can pull it off with old-fashioned deceit - calling up sites and services while posing as you, digging through your mail for documents, and getting around weak security questions with basic research. This can also extend to phishing attacks, where a subject is tricked into downloading malware, entering sensitive information into imposter websites, or revealing information that can help abusers compromise their information. Frequently, harassers will even register sockpuppet accounts on social media and try to befriend you in order to gain access to your social media information or undermine your confidence and security.
The best tactic for combatting social engineering hacks is old-fashioned preparedness and awareness. For the sake of common sense, here are a few pointers to know:
Try to avoid having one single point of failure in your security chain, or one bit of information that, if compromised, will betray the rest. If there’s one single thing that would screw you over if it got compromised or discovered, syndicate the risk across multiple services and security barriers. For instance, consider using a private, non-primary email address exclusively for password recovery options on websites; This way, if someone gains access to your primary email, they will be unable to reset other passwords from it.
While most legitimate IT/finance companies will never ask you for login or personal information via email or phone, you may get the occasional request. Deal with those by asking for a number to call them back, and verify online that it’s a legit number. Be extremely suspicious of unrequested password reset or login emails, and always pay attention to the URL when directed to a page that requires login to make sure it’s legit. Healthy suspicion is just that: healthy. Additionally, consider installing browser extensions like NoScript if you go to sites that may not be the most reputable of places, but know that they make browsing a bit of a PITA.
Make it a general practice to not friend people you don’t know on Facebook without confirmation, especially while you are being targeted. If you are worried that an incident of mob harassment is inevitable and have been in the practice of adding people liberally, consider revisiting your friends list and purging anyone you don’t explicitly trust, or yanking down statuses/photos that might reveal information you don’t want in the hands of an angry mob. This is one of the most frequent vulnerabilities we see exploited during episodes of mob harassment, and something we will expand on in forthcoming posts.
If you are currently being targeted by online harassment, do not rule out the possibility that someone who you’re talking to may not be the person they claim to be. If you get any requests for sensitive information from an unfamiliar account, it’s not too paranoid to spend a few seconds finding out who is asking. Is someone claiming to be press? Google the email address that they’re emailing you from and ask for previous articles they’ve written or other credentials if you have any concerns. Is someone messaging you from an account claiming to be someone you know, and acting a little off or asking questions they might not normally? Verify their identity in another format if you have doubts.
If you ever need to come up with a PIN or 4 number passphrase for any service ever, do not use your birth year. That is literally as insecure as making your password “password”. This includes the pin to your voicemail if you have one - often when people are doxed, voicemails will be compromised and occasionally hijacked (and occasionally used for SWATing attempts). Make sure you’re checking that if you find yourself having your cell phone number out there.
Additionally, ensure that your account PIN with your cell phone provider is not the same account PIN as your voicemail. If your voicemail becomes compromised, it becomes that much more dangerous if a hijacker can gain access to your entire account with the same number.
When chatting on any social media with people and the topic of sensitive information comes up, remember that nothing is ever really off the record, even if gchat says it is. Delete your logs if you ever have to send someone a password to a shared account (make sure they do the same), or ideally, use a method that’s not online at all like texting or voice chat. You can even split information like numbers and URLs over multiple networks to reduce the chance of intruders putting it all together. As an extension of this, realize that when you’re transmitting sensitive information online, you have to account for the other person’s security measures as well. Keep that in mind if you need to discuss anything that could compromise your account (or physical) safety. People are also unpredictable - be wary of what you tell people in anything other than total confidence.
When choosing security questions, try to get creative and make them unique or unresearchable. There are also a number of other tricks you could use, such as answering questions with all the keys shifted over, or using non-sequitur answers only you would know. You can also use password managers like Keepass to generate unique passwords for answer fields and track them within the manager. Sometimes you’ll find yourself having to choose from a list of drop-down questions that anyone with google can search for - in that case, consider having two passphrases that you use instead of the actual answers to that question, that are totally nonsensical and inapplicable.
If your financial institutions are forcing a default “mother’s maiden name” type question and answer system without room for varied input, consider calling them and explaining your concerns - or just use something different anyway, though keep in mind that it will be hilarious to say that your first pet’s name was Ptzq#!k. They can deal. Generally they are understanding and will work with you - and while you’re at it, make sure to work with them to make sure that nobody can access your banking information with your SSN, which may be easy to acquire. Many banking breaches occur with this kind of identity spoofing, not a hard hack.
Well, this all sounds like a pain in the ass.
True, it’s not as simple as a single universal password. But until we enter the brave new world of biometrically locked data, it pays to be careful (and even then, you can bet people will try to clone your finger just to gain access to your Gamestop account). We’re thankfully at a point where just a little common sense and a few sleek programs mean all the difference. Thirty minutes of setup and review could mean a lifetime of breathing easy. Why wait?







